The Challenge: Circuit Vulnerabilities
While the math is secure, the code (circuits) is fragile. Developers struggle to correctly implement circuits, leading to two opposing types of bugs. zkFuzz provides a unified framework to detect both:
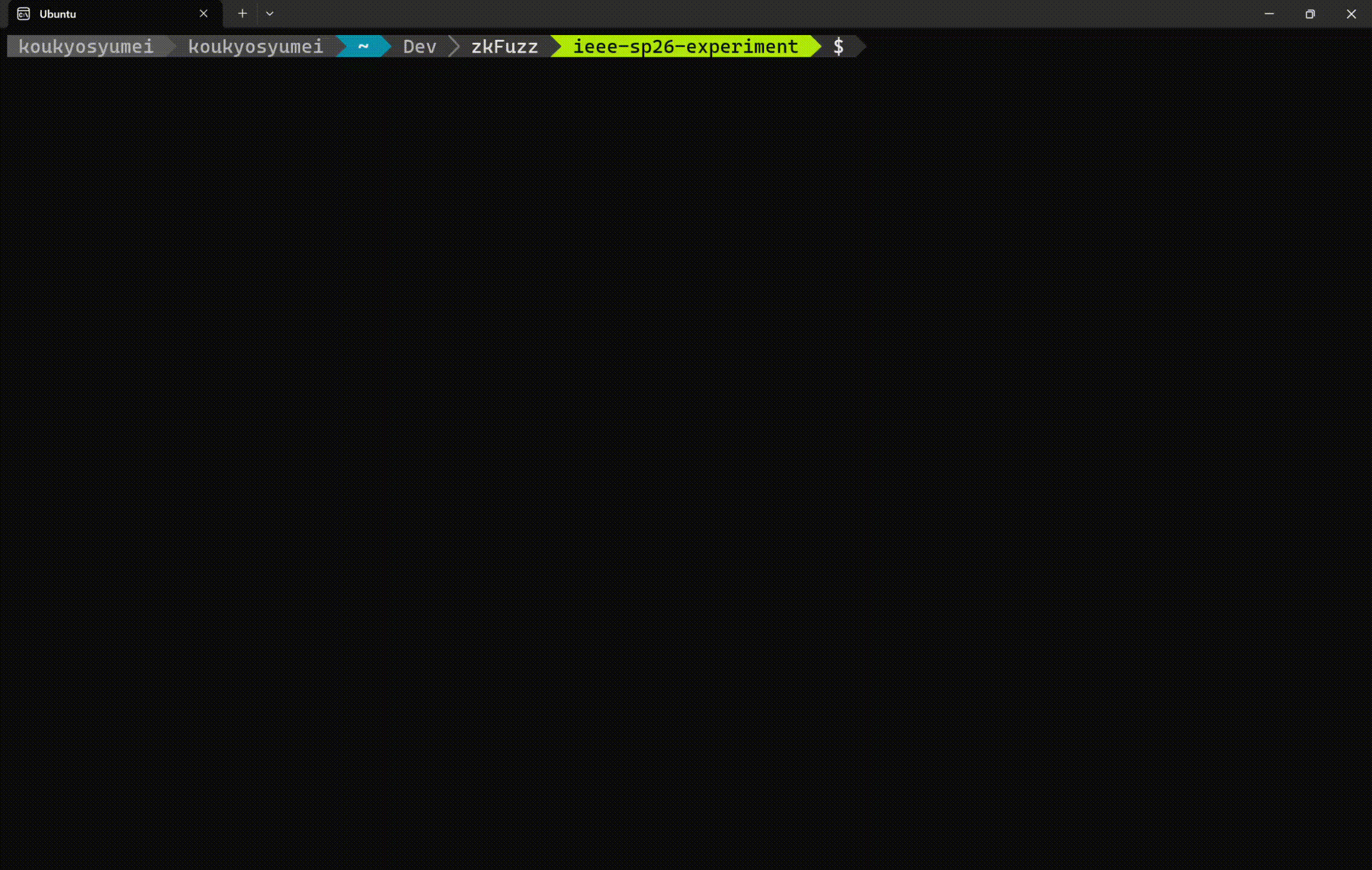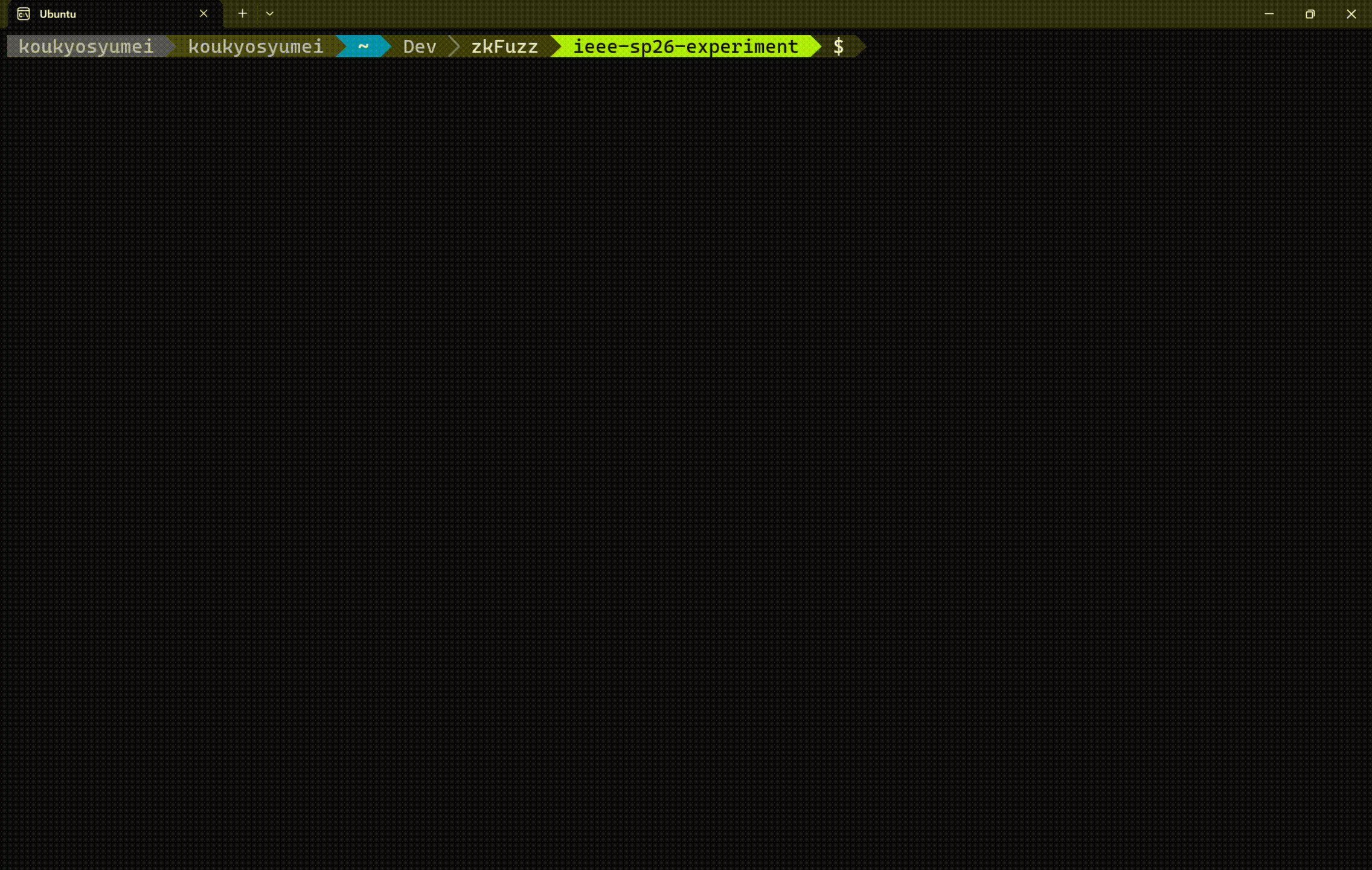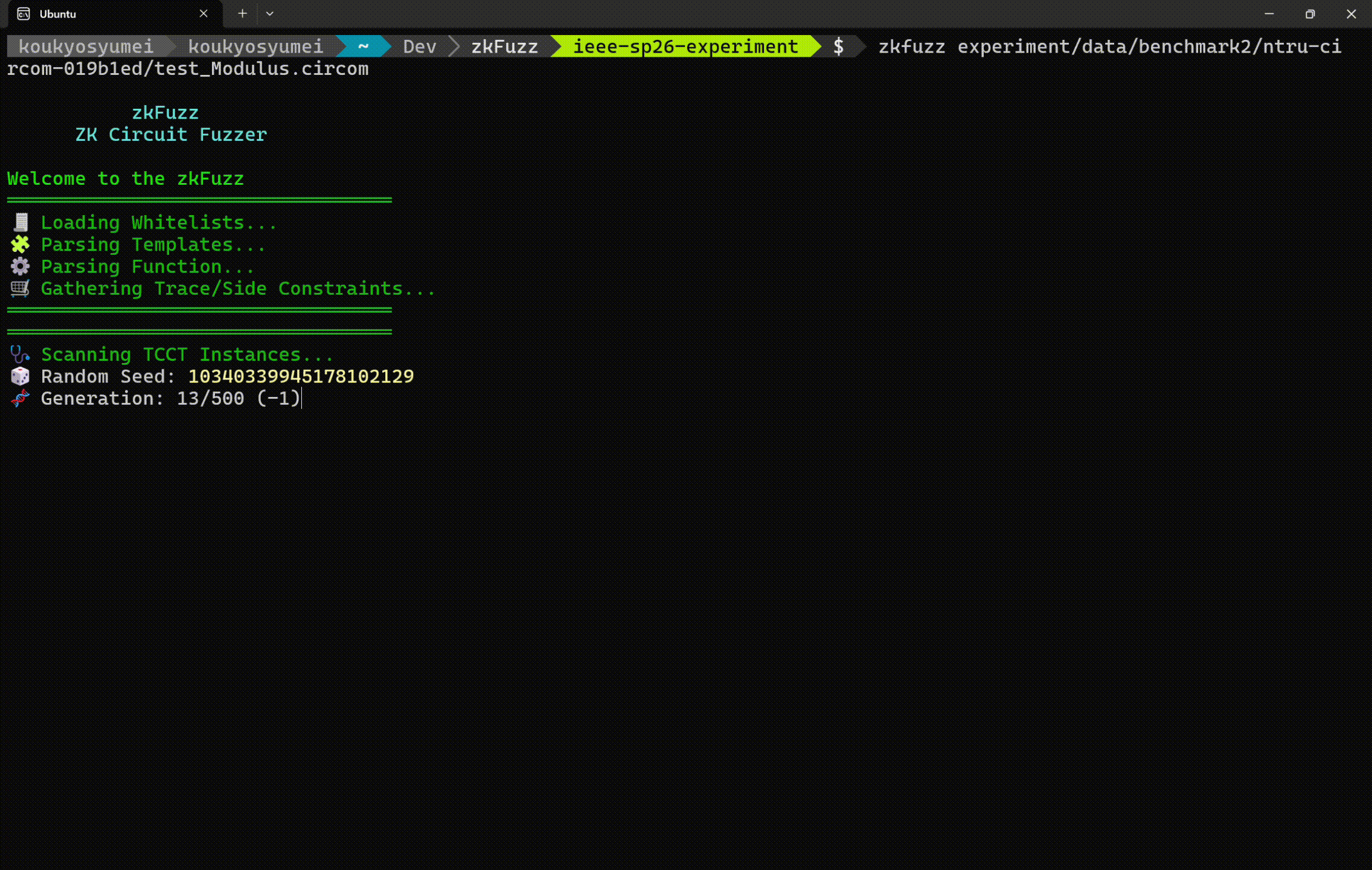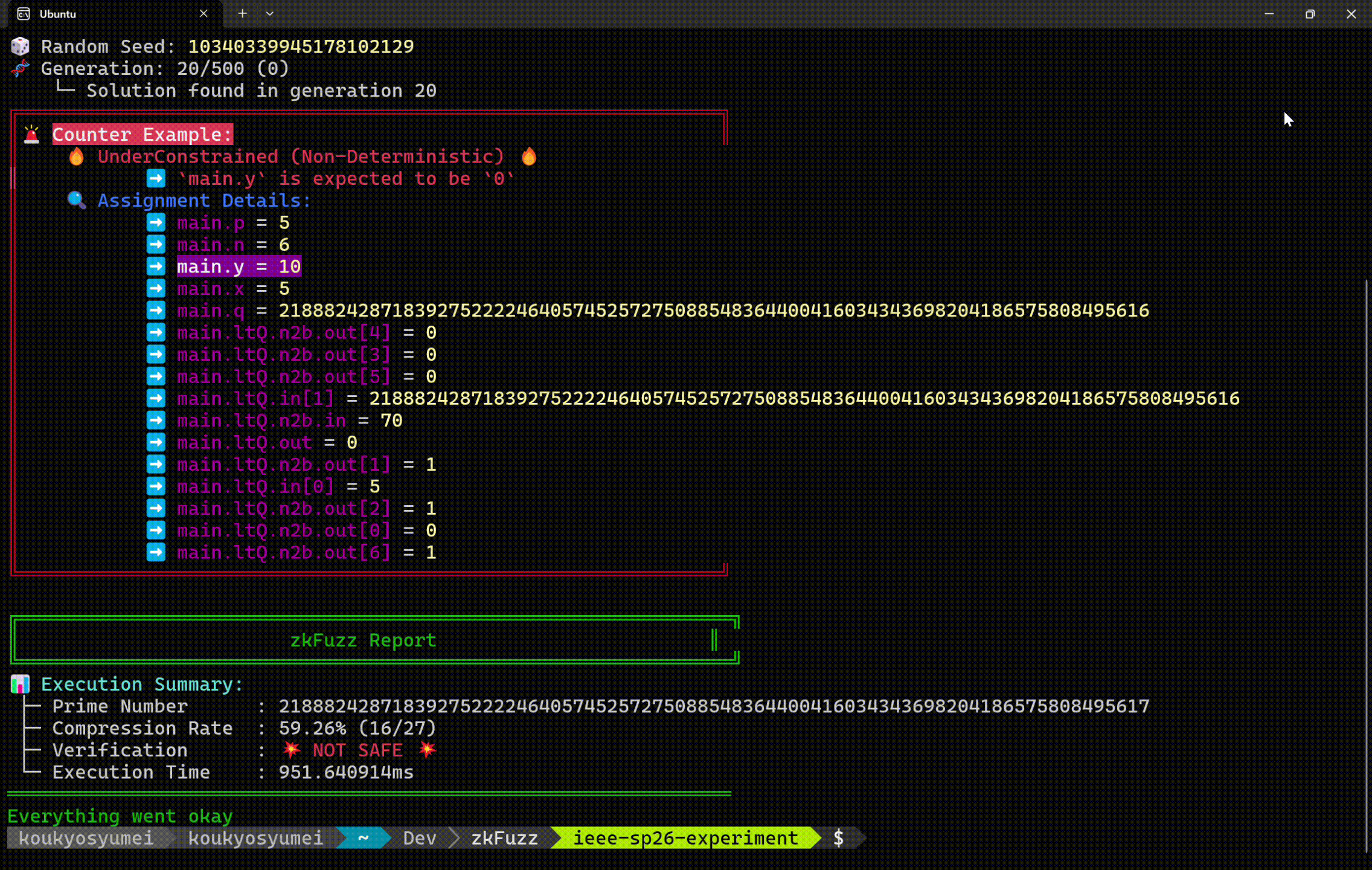
Under-constrained
(Soundness Error)
Missing constraints allow attackers to forge proofs for false statements (e.g., stealing funds).
Over-constrained
(Completeness Error)
Excessive constraints cause the system to reject valid proofs from honest users (DoS).